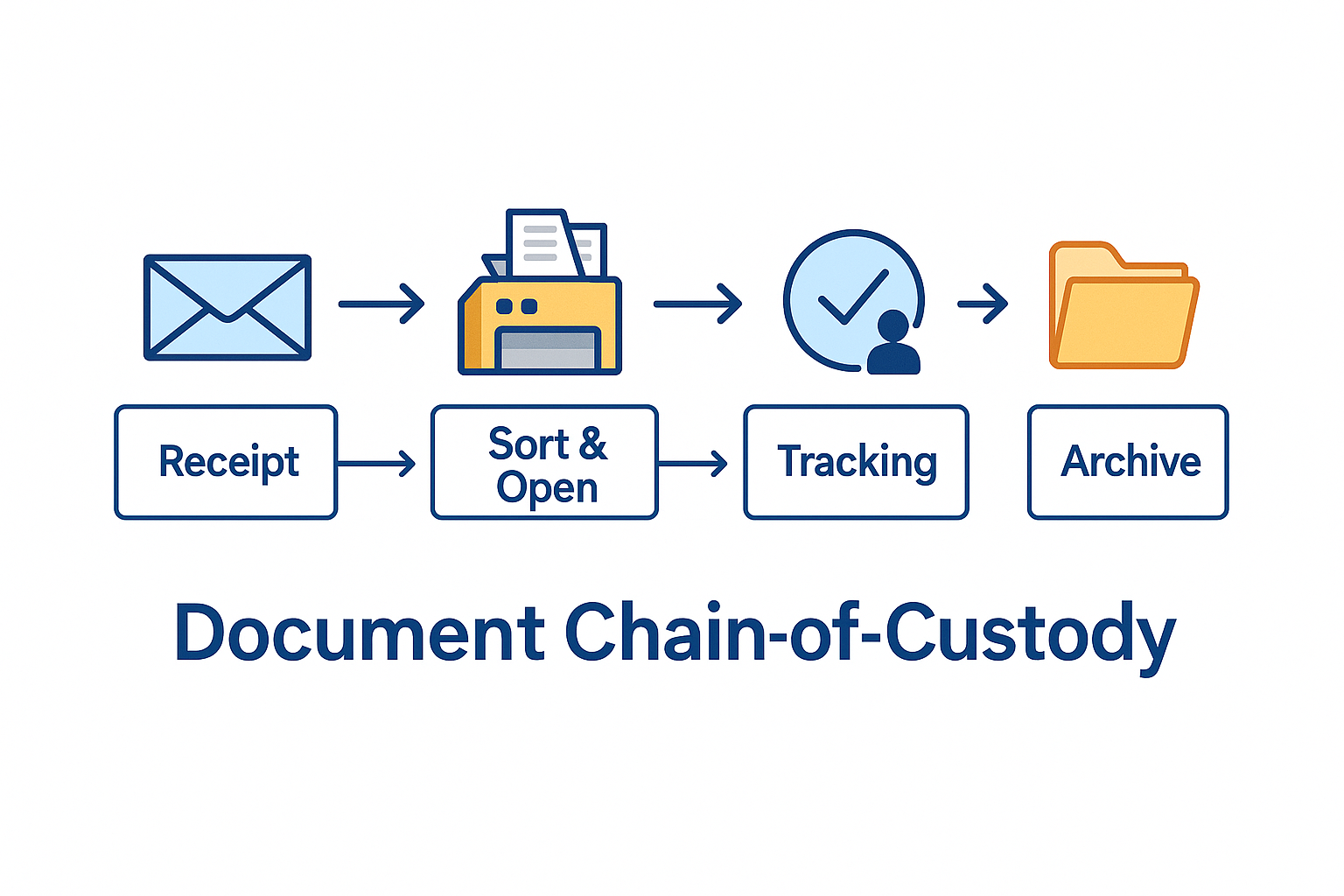
In industries where data integrity is non-negotiable, document traceability has become a compliance and operational mandate. Whether handling legal filings, ballots, financial statements, or patient records, the chain of custody — the documented and unbroken trail showing who had access to a document and when — is critical to preventing data breaches, maintaining regulatory compliance, and building organizational trust.
Agissar’s advanced automation technologies are built not just to process envelopes but to preserve accountability at every step of the document journey.
Why Chain-of-Custody Matters More Than Ever
A weak or undocumented chain of custody creates room for error, fraud, or costly non-compliance. For example:
-
In legal cases, missing timestamped tracking can invalidate key evidence.
-
In elections, it may cast doubt on ballot integrity.
-
In finance, it risks violations of regulations like SOX (Sarbanes-Oxley Act).
-
In healthcare, it may breach HIPAA compliance.
Maintaining a secure and auditable trail of document handling isn’t just best practice — it’s a regulatory expectation.
Manual Mailroom Handoffs: A Risky Business
Legacy systems rely on handwritten logs, verbal handoffs, or siloed spreadsheets to track sensitive documents. These manual methods are:
-
Prone to human error
-
Difficult to audit retroactively
-
Vulnerable to tampering or document loss
-
Inefficient for high-volume environments
This opens the door to lost information, regulatory breaches, and legal liability — all of which can be avoided with automation.
Agissar’s Chain-of-Custody-First Approach
Agissar redefines how organizations manage secure document flow by embedding audit trails into the document lifecycle itself.
🔐 Key Capabilities Include:
-
Real-Time Activity Logging
Every interaction with a document — from envelope opening to scan verification — is logged with user credentials, timestamps, and machine data. -
Seamless Envelope Tracking
Agissar’s automated sorting and extraction systems create a digital fingerprint of each document. You always know where it came from, where it is, and where it’s going. -
Integration with INFOPoll® and INFOPointe™
These systems capture, verify, and tag documents with full compliance metadata as soon as they’re processed — no added labor required. -
Tamper-Resistant Audit Trails
Immutable logs ensure that no action goes undocumented or can be quietly altered.
Chain-of-Custody in Action: Real-World Example
A national insurance carrier processing thousands of claim forms per day turned to Agissar after facing internal audit failures related to unverified mail handling. With INFOPoll® and WebWarehouse® integrated:
-
99.7% of all mail events were logged automatically
-
Retrieval time for any specific document dropped from 48 hours to under 10 minutes
-
They passed their next compliance audit with zero findings
Industry Applications
Chain-of-custody is critical in:
| Industry | Why It Matters |
|---|---|
| Legal | Track discovery documents and official court communications |
| Finance | Ensure integrity of transactional data under SOX regulations |
| Healthcare | Secure patient records and maintain HIPAA chain-of-access |
| Elections | Validate ballot reception, processing, and storage |
| Government | Manage secure correspondence and FOIA-requested documents |
Seamless Deployment and Legacy System Compatibility
Agissar’s chain-of-custody tools plug into legacy mailroom equipment or workflows with minimal disruption. You don’t have to rip and replace your current setup to move toward traceable, secure mail operations.
Deploying a new technology in any production environment—especially one that handles mission-critical document workflows—often triggers concern about downtime, cost, and integration complexity. Agissar understands this hesitation and has engineered its mail extraction and document processing solutions with plug-and-play compatibility in mind.
⚙️ Built for the Realities of Existing Infrastructure
Agissar’s systems, including their industry-leading mail opener machines and automated document capture technologies, are designed to be hardware-agnostic and software-flexible. Whether you’re working with an outdated ERP system, a custom in-house database, or third-party records management software, Agissar’s platforms can be integrated without requiring a ground-up IT overhaul.
Example: A major insurance provider with a 15-year-old mainframe-based data system was able to deploy Agissar’s INFOPoll® technology without reconfiguring their backend software. The result? Full functionality within two weeks and zero disruption to ongoing claims processing.
🔁 API Connectivity & Middleware Integration
Agissar’s mail extraction solutions offer robust RESTful API support, making them easy to interface with modern platforms like:
-
Microsoft Dynamics
-
Oracle Fusion Middleware
-
SAP
-
IBM FileNet
-
SharePoint
-
Custom .NET and Java-based applications
For older systems or unique requirements, Agissar supports middleware bridging to ensure data flow remains uninterrupted—even when operating within environments lacking modern APIs.
🕒 Minimal Downtime, Maximum Continuity
Implementation typically follows a phased rollout model that allows organizations to maintain full operations during deployment. Key features include:
-
Pre-installation system mapping and compatibility checks
-
Simulation testing using sample document batches
-
Optional parallel processing mode, enabling teams to verify Agissar’s accuracy while still running legacy systems in tandem
-
Staff onboarding and real-time remote support during transition
This approach ensures organizations don’t experience the “rip and replace” stress associated with many enterprise tech rollouts.
🔐 Compliance, Logging & Security from Day One
Even during integration, Agissar ensures all document-handling events are logged, encrypted, and auditable. This meets industry standards for:
-
HIPAA (Healthcare)
-
SOX (Financial services)
-
GDPR (EU data privacy)
-
CCPA (California privacy regulation)
All logs and data interactions are compliant with your regulatory environment out of the box, meaning there’s no need for separate configuration of audit trails post-deployment.
🧠 Smart Learning for Your System Nuances
Agissar’s intelligent automation doesn’t just process data—it learns your document patterns. Through configurable templates and AI-assisted routing rules, the system adapts to:
-
Your mail volume rhythms
-
Specific document types (e.g., ballots, applications, invoices)
-
OCR variations in scanned materials
-
Priority handling flags (e.g., urgent legal docs)
This learning reduces the need for custom coding while future-proofing your investment—the more it works, the smarter it gets.
Conclusion: Don’t Leave Trust to Chance
When documents matter, who touched what and when matters even more. With Agissar’s full-spectrum automation and chain-of-custody tracking, you gain control over your mailroom, accountability in your operations, and confidence during audits.
➤ Ready to eliminate risk and build trust?
Contact Agissar to learn how chain-of-custody automation fits into your current workflow.
Table of Contents
Share This!

Agissar not only has a history of game-changing advances in the mail extraction industry, we also have a stellar reputation for excellent products, services and attention to detail that has been built over decades. It shows in our relationships with suppliers, clients, and our ability to get excellent value for your dollar while supporting a wide range of mailing, imaging, and office products from the simple to the complex. We can custom tailor service programs to meet your needs and help you get to the top of your industry, all you need to do is contact us today!